SameSite Cookies with IIS
By Pete Freitag
SameSite cookies are a great technique for mitigating Cross Site Request Forgery attacks. The only downside is that not all browsers support them yet (ahem... looking at you IE).
Another downside you may find is that most application server software does not support them yet, for example javax.servlet.http.Cookie does not yet have support, PHP has a RFC and hopes to add them in 7.3, ASP.NET Core has added them to 2.0 and .NET Framework 4.7.2.
ColdFusion has added support for samesite cookies (after the original publication of this entry) in the cfcookie tag in ColdFusion 2018. You can also set samesite values on session cookies as of CF2018+ via this.sessionCookies, or in the ColdFusion Administrator.
If your current platform doesn't support them yet but you want to use them, then you can use the web server to append the SameSite attribute to the Set-Cookie http response header.
Here's how you can do it in IIS using the IIS URL Rewrite Module:
- Install Microsoft URL Rewrite for IIS: https://www.iis.net/downloads/microsoft/url-rewrite
- Close IIS, and open it again.
- Click On the root server level node of IIS (so that this is applicable to all sites on your server),
- Double Click on the URL Rewrite icon
- Click on Add Rule(s)
- Under Outbound Rules select Blank Rule
- Give it an arbitrary name, eg
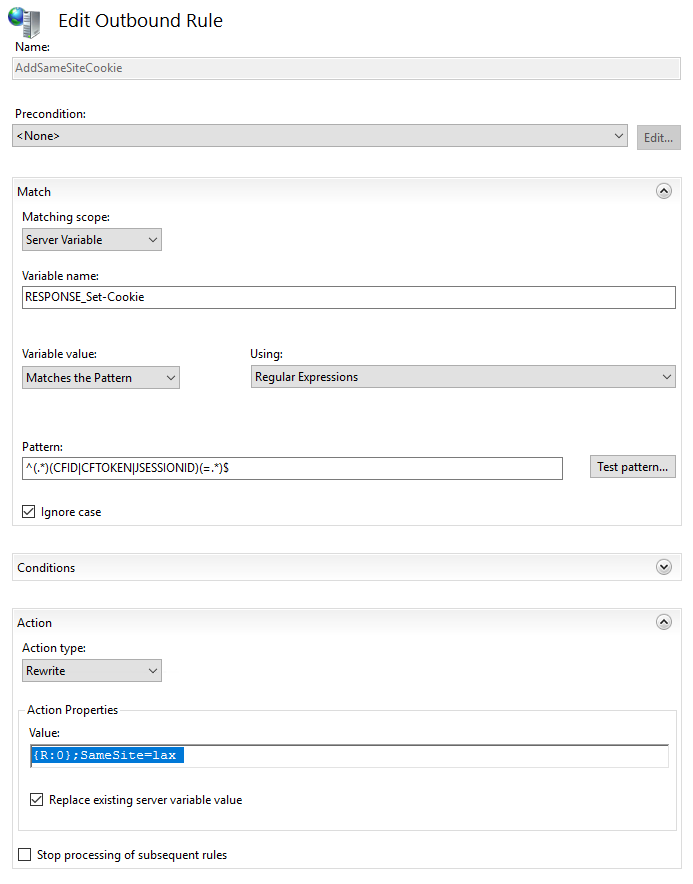
AddSameSiteCookieFlag - Under Match, select Matching Scope:
Server Variable - For Variable name use:
RESPONSE_Set-Cookie - Variable Value:
Matches Pattern - Using:
Regular Expressions - Pattern:
^(.*)(CFID|CFTOKEN|JSESSIONID)(=.*)$(that only applies to cookies namedCFIDECFTOKENorJSESSIONID, modify as needed) - Under Action, Action Type:
Rewrite - Action Properties: Value:
{R:0};SameSite=lax(if your existing cookie has a trailing semi-colon you can remove it here, you may also consider usingStrictinstead ofLax). - Check Replace existing server variable
Or here's how you can add it to a single site using web.config files:
<rewrite>
<outboundRules>
<rule name="AddSameSiteCookieFlag">
<match serverVariable="RESPONSE_Set-Cookie" pattern="^(.*)(CFID|CFTOKEN|JSESSIONID)(=.*)$" />
<action type="Rewrite" value="{R:0};SameSite=lax" />
</rule>
</outboundRules>
</rewrite>
SameSite Cookies with IIS was first published on May 14, 2018.
If you like reading about iis, cookies, samesite, or security then you might also like:
- Remove the Server Header in any IIS Version
- SameSite cookies with Apache
- Blocking .svn and .git Directories on Apache or IIS
- Client Variable Cookie CFGLOBALS Includes Session Ids
The FuseGuard Web Application Firewall for ColdFusion & CFML is a high performance, customizable engine that blocks various attacks against your ColdFusion applications.
CFBreak
The weekly newsletter for the CFML Community
Comments
Does this still apply?
This rewrite outboundrule is perfactly working in firefox but it is not working in chrome.
Please help me.
 Pete Freitag
Pete Freitag
And in case anyone misses it in the related posts links above, note that he covered apache in a later post:
https://www.petefreitag.com/blog/samesite-cookies-apache/
And before someone asks, support is due to be added to cf (2018 and 2016) in a coming update (yes, frustratingly late). But this should help folks until then, and also those on earlier CF versions.